Automatic Identity Management for Entra ID is now Generally Available in Azure Databricks
Instantly connect users, groups, and service principals for faster setup and collaboration
Summary
• Automatic Identity Management (AIM) for Entra ID on Azure Databricks is now Generally Available, removing the need for manual provisioning or complex SCIM-only workflows.
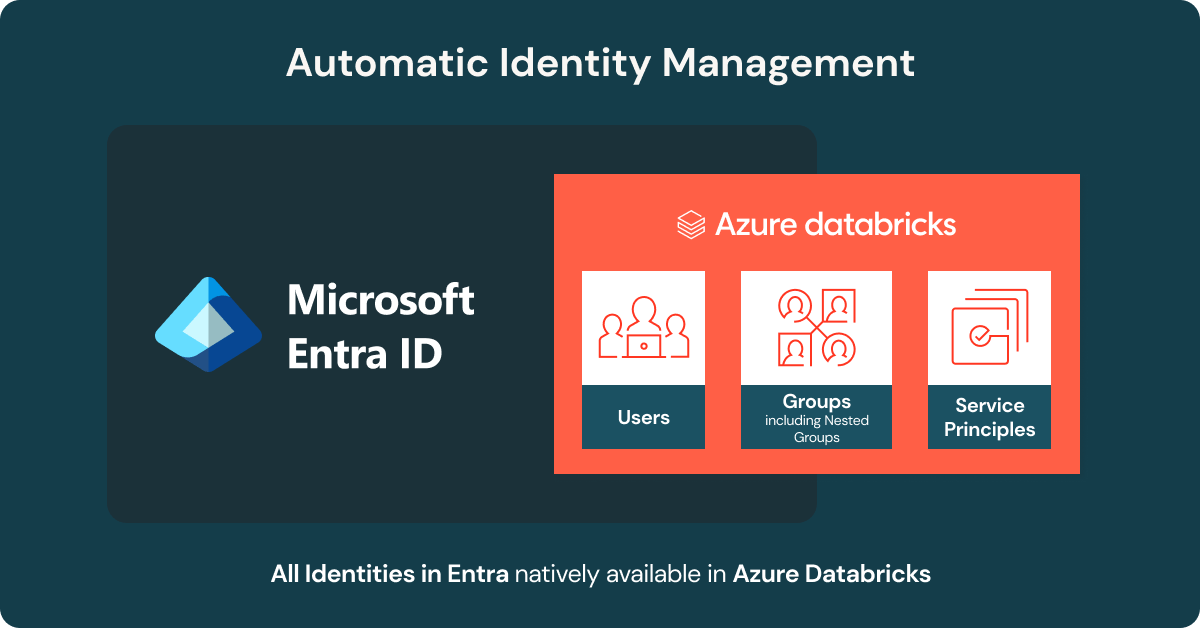
• With AIM, users, groups, and service principals are automatically available within Azure Databricks, with support for nested groups and dashboards.
• The GA release makes AIM on by default for new accounts, offers a simple opt-in for existing ones, and adds API support for automation at scale.
Automatic Identity Management (AIM) for Entra ID on Azure Databricks is now Generally Available.
As customers scale their use of Databricks, managing thousands of users, groups, and service principals across teams becomes complex. Traditionally, admins have relied on SCIM, custom scripts, or manual setup to provision access and keep identities in sync. While these approaches work, they add overhead and make it harder to keep up with fast-growing identity environments.
AIM changes this. Users, groups, and service principals from Entra ID are now connected automatically, so you no longer need to pre-provision identities. This means faster onboarding, less manual work, and smoother collaboration. For example, you can now share an AI/BI dashboard with anyone in your Entra ID directory, even if they’ve never logged into Databricks before.
In this post, we’ll discuss the GA release's features and how AIM works in practice.
What’s new in our General Availability release
Automatic Identity Management for Entra ID is available today as part of our ongoing collaboration with Microsoft. As a first-party service on Azure, Databricks continues to deliver native integrations that help customers simplify operations and scale securely. With this GA release, Automatic Identity Management (AIM) for Entra ID brings several important updates for Azure Databricks customers to help with adoption and scalability:
- On by default for new accounts: Every new Azure Databricks account now has AIM enabled automatically. Admins can skip manual provisioning and start with less overhead from day one.
- Simple opt-in for existing accounts: Existing accounts can enable AIM anytime with a single toggle in the Account Admin Console. In the coming months, AIM will become the default across all accounts.
- API support for automation: APIs are now available to programmatically register Entra users, groups, and service principals. This makes it easier to handle large-scale onboarding, scripted automation, or partial provisioning setups.
"Automatic Identity Management creates a seamless identity management experience in Azure Databricks. It delivers the enterprise-grade user and group management our teams need and adds meaningful maturity to the platform, especially important at our scale, with over 43,000 groups."- Yev Eydelman, Analytics & AI Lead, CARIAD (Volkswagen Group Company)
How Automatic Identity Management Works
Gartner®: Databricks Cloud Database Leader
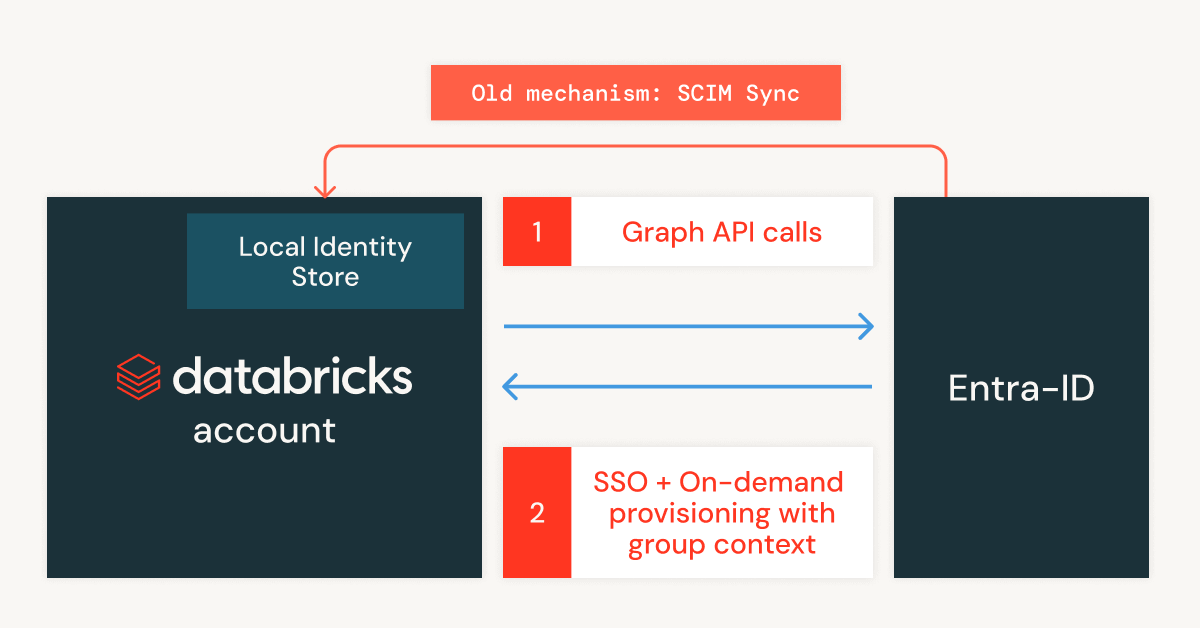
With AIM, Entra users, service principals, and groups are available in Azure Databricks as soon as they’re granted permissions. Group memberships, including nested groups, flow directly from Entra ID, so permissions always reflect the latest updates.
Under the hood, AIM uses the Entra ID Graph API to keep the Databricks identity directory in sync. It works seamlessly with SCIM, supports service principals (even inside groups), and treats all identities consistently across workspaces.
"Automatic Identity Management will allow us to sunset a large, bespoke integration we had to build ourselves, including a self-service API, and shift identity management directly to our Databricks users. That’s a huge step forward in scaling access securely and efficiently across our organization." - Gerco Grandia, Lead Solutions Architect, E.ON
For collaboration, this means:
- Sharing an AI/BI dashboard is immediate — no pre-provisioning needed.
- Permissions follow Entra ID profiles in real time.
- Even users who are not workspace members can view dashboards if they’re shared with embedded credentials.
See how it works in our demo, and consult the documentation for full details, as well as our blog on the Microsoft Tech Community.
Never miss a Databricks post
What's next?

Product
November 21, 2024/3 min read

