Reference Architecture for Security Operations
Build faster, smarter security operations using Databricks to detect threats, hunt anomalies and enrich alerts. This architecture connects data from SIEM, identity, endpoint and threat intel into a unified investigation and response workflow.
Strengthen core security operations
This reference architecture outlines how security operations teams can build and scale core security operations capabilities on the Databricks Data Intelligence Platform. It centralizes telemetry, enables structured enrichment and transformation, and powers advanced workflows across detection engineering, threat response, compliance and reporting.
Architecture overview
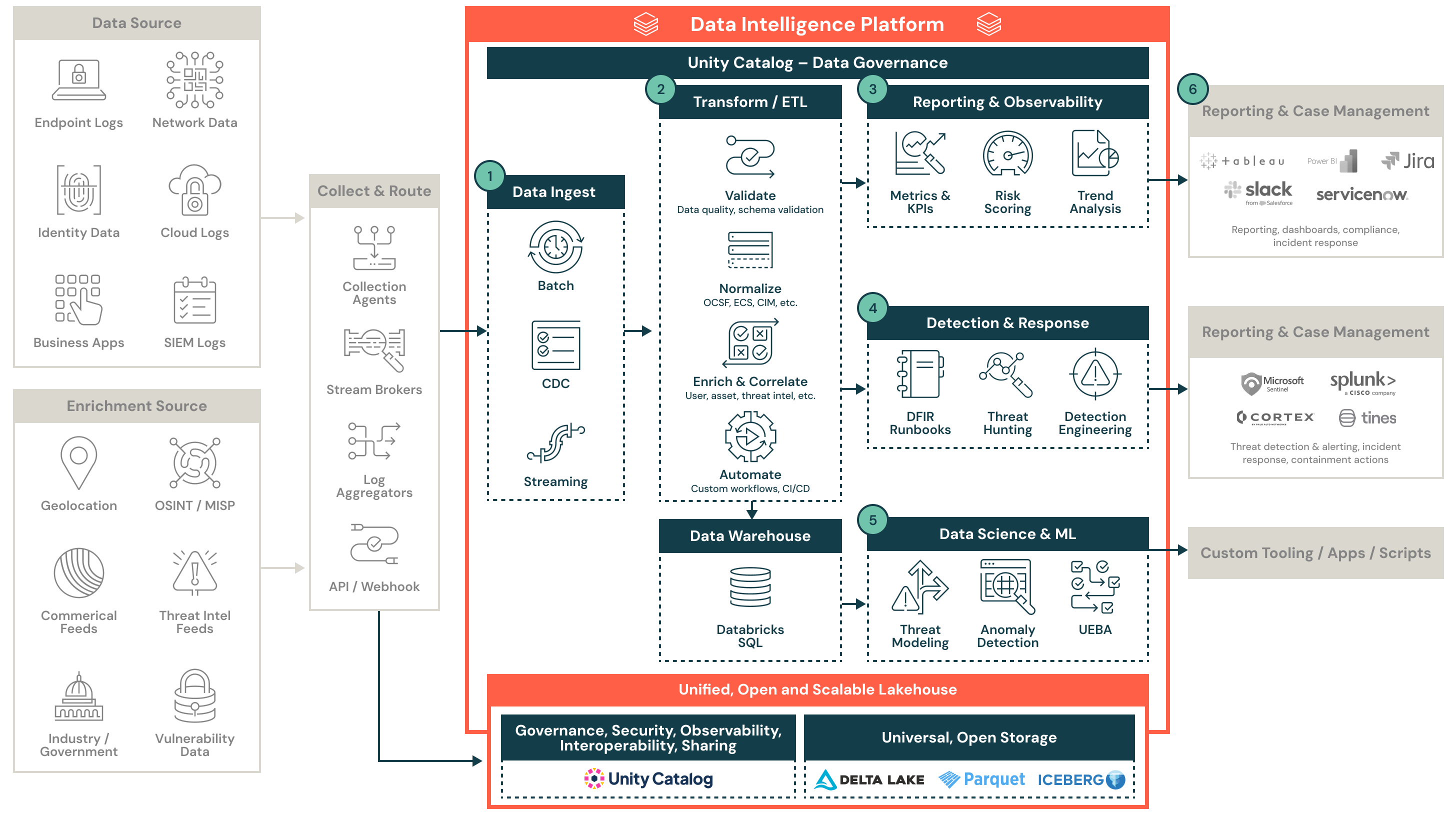
Security operations teams rely on flexible, data-driven workflows to manage threat detection, response and compliance at scale. Legacy architectures often separate detection, investigation and reporting across disconnected systems. The security lakehouse for security operations unifies these capabilities by combining governed storage, open analytics and scalable automation in a single platform.
This architecture illustrates how telemetry from endpoint, identity, network and cloud sources flows into the lakehouse using batch and streaming pipelines. Security teams can validate and normalize this data using open schema models such as OCSF, ECS or CIM. Events are enriched with user, asset and threat context to improve detection quality and investigative outcomes.
Once processed, this data powers a wide range of security operations use cases, including alerting, threat hunting, detection engineering, metrics reporting and anomaly detection. Curated outputs can be integrated with SIEMs, SOARs, case management systems and reporting tools to support incident workflows and cross-team collaboration.
Collect and route
Telemetry and threat intelligence are collected using agents, brokers, aggregators and APIs. This step supports structured and unstructured formats and enables both real-time and batch ingestion. Data sources include endpoint logs, identity events, cloud telemetry, vulnerability data and commercial threat feeds.
Transform and enrich
Raw data is validated for quality and schema alignment, then normalized and enriched for operational use. Enrichment can include user, device, application, threat intel and asset context. Schema models such as OCSF and ECS help standardize fields for analysis and automation.
Reporting and observability
Security analysts and stakeholders use structured data to build dashboards, visualize trends and track key metrics. These outputs help teams monitor coverage, identify gaps and meet compliance and audit requirements.
Detection and response
Detection engineers create and manage rules for identifying threats and suspicious behavior. Alerts feed into incident response workflows, DFIR runbooks and threat hunting investigations. Teams can orchestrate playbooks or push alerts to case management systems.
Data science and ML
Security teams can apply machine learning models for advanced analytics and detection. Use cases include threat modeling, behavioral baselining, anomaly detection and user entity behavior analytics. These models improve prioritization and reduce false positives.
Integrate with external systems
Curated alerts, dashboards and context are delivered to downstream platforms such as SIEM, SOAR, reporting and ticketing systems. This allows Databricks to serve as the analytical backbone while preserving familiar analyst workflows in tools like Splunk, Sentinel, Jira and ServiceNow.

