Lakehouse for Cybersecurity Applications
Lower costs, reduce complexity and mitigate threats
The lakehouse unifies your data stack, securely
Learn more
The Lakehouse Effect
85%
Of queries completed in under 7 seconds
10GB
Of data ingested related to security events per second
Ingestion
Time reduced from 15 minutes to under 1 minute
Akamai runs a pervasive, highly distributed content delivery network (CDN). Its CDN uses approximately 345,000 servers in more than 135 countries and over 1,300 networks worldwide to route internet traffic for some of the largest enterprises in media, commerce, finance, retail and many other industries. About 30% of the internet’s traffic flows through Akamai servers. Akamai also provides cloud security solutions. In 2018, the company launched a web security analytics tool that offers customers a single, unified interface for assessing a wide range of streaming security events and performing analysis of those events. The web analytics tool helps Akamai customers make informed actions in relation to security events in real time.

Solution Accelerators
Databricks-developed solutions to deliver the data and AI-driven outcomes that matter most — faster
Databricks Solution Accelerators are purpose-built guides — fully functional notebooks and best practices — that speed up retail results. Save time on discovery, design, development and testing in use cases like IOC matching, context graph analytics and incident investigation.
Partner Solutions
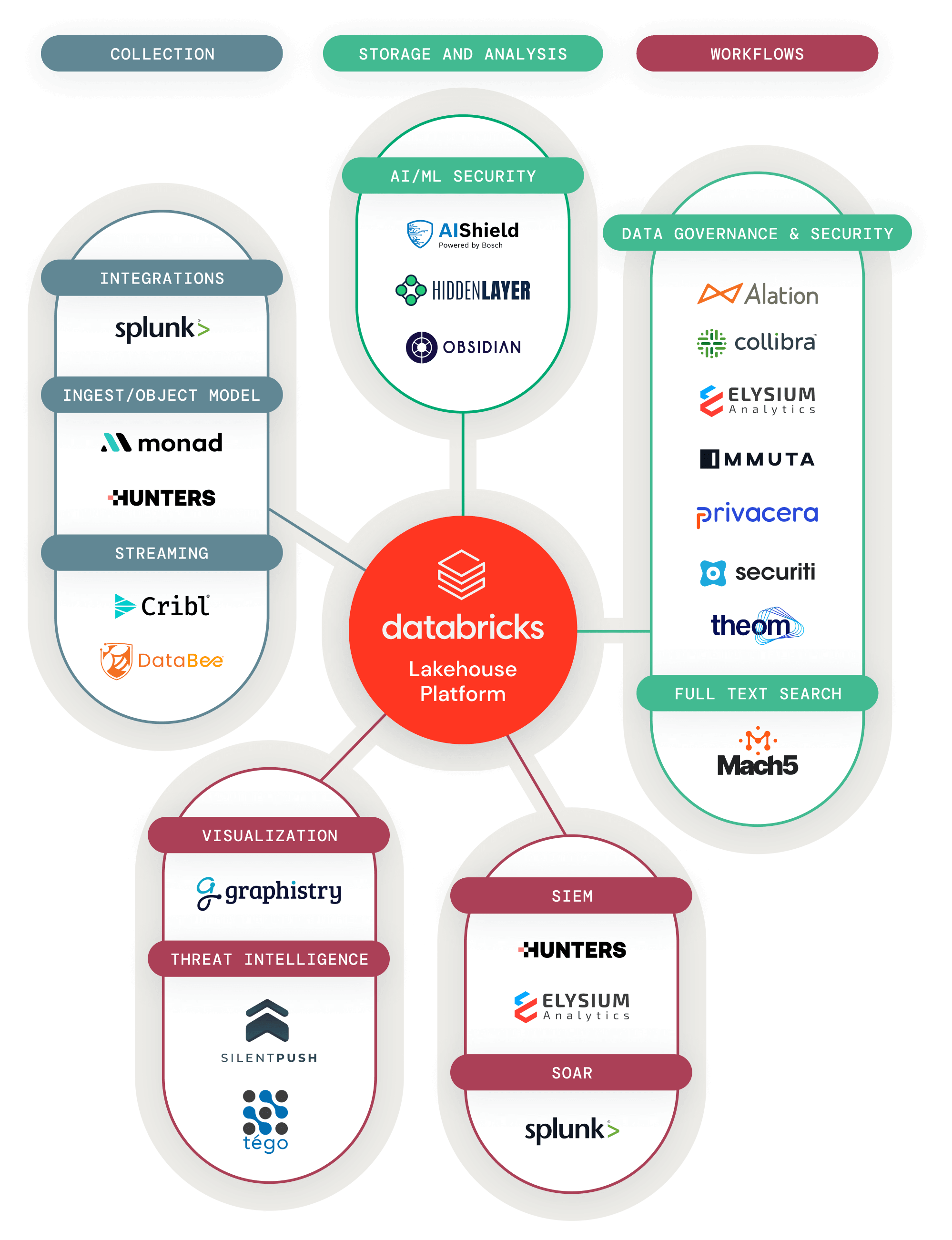
Easily discover and integrate data, analytics and AI solutions with your lakehouse
Partner Connect makes it easy for you to discover data, analytics and AI tools directly within the Databricks platform — and quickly integrate the tools you already use today. With Partner Connect, you can simplify tool integration to just a few clicks and rapidly expand the capabilities of your lakehouse.