Security & Trust Center
Your data security is our top priority
Protect Your Data With the Enhanced Security and Compliance Add-On
At Databricks, we recognize that maintaining data security and compliance is a top priority for our customers. That is why Databricks is introducing the Enhanced Security and Compliance Add-On to help simplify the complexity of meeting security and regulatory requirements for our customers.
What is the Enhanced Security and Compliance Add-On?
The Enhanced Security and Compliance Add-On is made up of two features:
With Enhanced Security Monitoring, we enable the use of enhanced hardened images, add additional security tools for behavioral-based malware monitoring and provide vulnerability reports for our images. Enhanced Security Monitoring is currently available on the AWS and Azure classic compute planes. The Compliance Security Profile builds on top of Enhanced Security Monitoring and provides features required for compliance, like FIPS 140 encryption and cluster update enforcement. The Compliance Security Profile is currently available on the AWS and Azure classic compute planes as well as the AWS us-east-1 region for AWS Databricks SQL Serverless workloads.
The benefits of using Enhanced Security Monitoring
On top of Databricks' existing security features, Enhanced Security Monitoring provides customers with increased visibility, threat protection and security hardening for their workloads. Benefits of this offering include:
-
A Canonical Ubuntu Advantage with enhanced CIS Level 1 hardening
-
Behavior-based malware monitoring and file integrity monitoring
-
Malware and antivirus detection
-
Vulnerability reports of the host OS¹
With Enhanced Security Monitoring, security event logs are delivered along with your regular Databricks audit logs, providing comprehensive security monitoring in your organization's SIEM or Databricks platform. These logs come with contextual information that assists analysts in quickly determining the origin of suspicious activity without requiring a lengthy investigation.
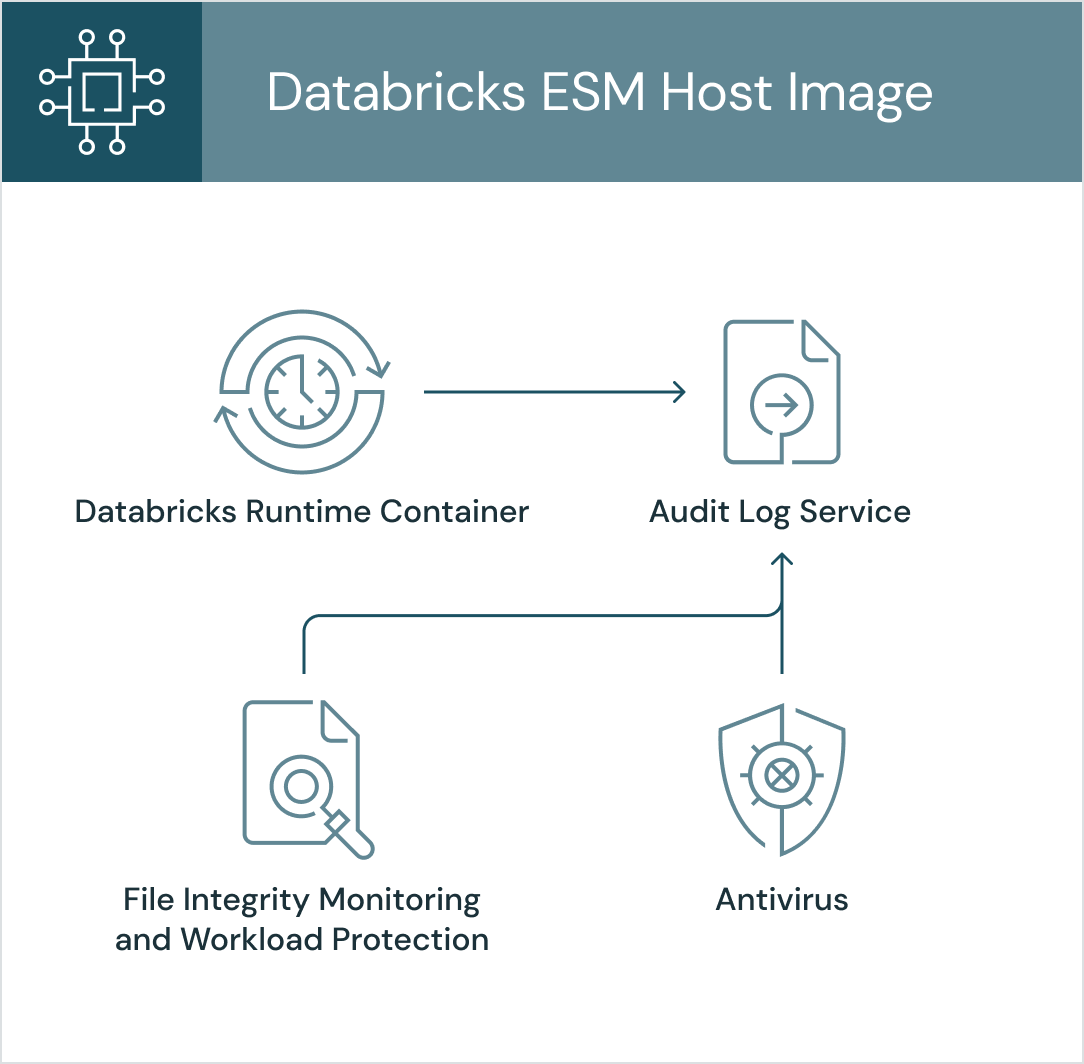
Figure 1: Audit logging of security features in the Enhanced Security Monitoring host image
1 Databricks classic compute plane only. Vulnerability scans are performed on a representative host image in the Databricks environment and reports are provided to customers on a biweekly basis.
Benefits of Compliance Security Profile
Compliance Security Profile (CSP) provides customers the means to run cloud-ready HIPAA, PCI-DSS and FedRAMP Moderate workloads. Compliance Security Profile is our most secure baseline for the data plane — and includes all of the benefits of Enhanced Security Monitoring — making it easier to meet and manage compliance control requirements. Key benefits of this offering include:
The ESM security enhancements listed above
FIPS 140 Level 1 validated encryption modules (where available)
AWS Nitro VM enforcement for data at rest and in transit encryption
Automatic Cluster Update with customizable maintenance window
How to Get Started
The Enhanced Security and Compliance add-on, including the Compliance Security Profile and Enhanced Security Monitoring, is now self-service for Account Admins and is managed via the Account Console. Admins can enable these features in two ways:
On existing workspaces by navigating to the Security and compliance tab in the Account Console.
By setting an account-level default to automatically apply the features to all new workspaces.